Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week.
Featured Analysis
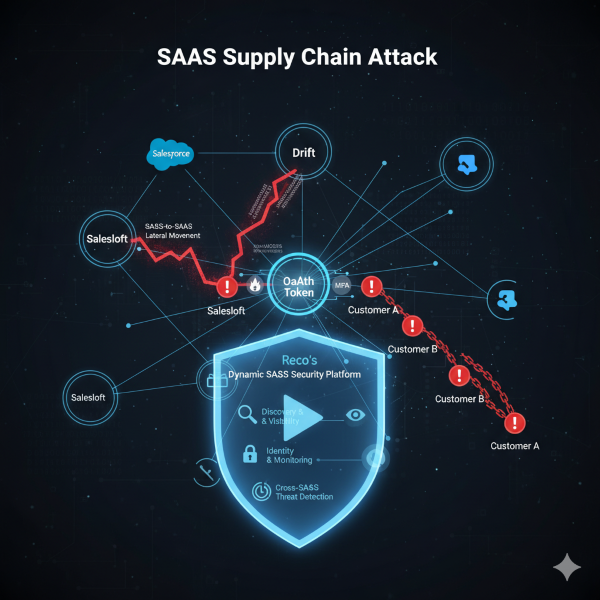
Featured article analysis: The Salesloft-Drift Breach: Analyzing the Biggest SaaS Breach of 2025
Analysis of The Salesloft-Drift SaaS Supply Chain Breach
This article effectively spotlights the most critical emerging threat in enterprise security: the SaaS supply chain attack leveraging unmonitored SaaS-to-SaaS integrations. The breach of Salesloft and Drift, attributed to sophisticated groups like ShinyHunters and Scattered Spider, serves as a powerful case study for a fundamental shift in risk. Since most modern businesses rely on an interconnected ecosystem of applications like Salesforce and Gmail, a compromise in a single low-profile third-party vendor offers a “10x force multiplier” for attackers, allowing them to pivot laterally into hundreds of downstream customer environments. This risk profile—where a company’s sensitive data is accessed not through a firewall failure but through a trusted connection and persistent OAuth token—is highly relevant to all LinkedIn professionals, especially those in leadership and IT/DevOps roles responsible for vendor risk and cloud security architecture.
The analysis of why “traditional SaaS security failed” underscores the growing SaaS Security Gap. Legacy security tools, designed for on-premise networks or simple SaaS usage, are blind to the five critical attack vectors: the persistent nature of compromised OAuth tokens, the ability for attackers to conduct SaaS-to-SaaS lateral movement, and the complete lack of visibility into these third-party connections. This is a direct challenge to the common belief that simply having an identity and access management (IAM) solution is sufficient, as IAM often trusts OAuth tokens by design. The article thus compels organizations to shift their focus from protecting the network perimeter to continuously monitoring the permissions, configurations, and behavioral patterns within and across their interconnected cloud applications.
The proposed solution, Dynamic SaaS Security from the article’s publisher, Reco, frames the next necessary evolution in defense. It details a multi-layered strategy that directly counters each attack vector by providing instant discovery of risky SaaS-to-SaaS connections, continuous monitoring of OAuth token usage, and cross-SaaS threat detection.1 For security professionals, this translates into actionable steps: prioritizing the active scanning and removal of secrets and API keys embedded in SaaS environments and implementing real-time behavioral policies that look for anomalous activity that spans multiple applications.2 Ultimately, the Salesloft-Drift breach is presented not just as a news event, but as a watershed moment proving that static, siloed security is obsolete in the era of hyper-connected cloud workflows.
Projects
Videos
Articles
- Discord discloses data breach after hackers steal support tickets – Hackers stole partial payment information and personally identifiable data, including names and government-issued IDs, from some Discord users after compromising a third-party customer service provider.
- CometJacking: One Click Can Turn Perplexity’s Comet AI Browser Into a Data Thief – Cybersecurity researchers have disclosed details of a new attack called CometJacking targeting Perplexity’s agentic AI browser Comet by embedding malicious prompts within a seemingly innocuous link to siphon sensitive data, including from connected services, like email and calendar.
- ParkMobile pays… $1 each for 2021 data breach that hit 22 million – ParkMobile has finally wrapped up a class action lawsuit over the platform’s 2021 data breach that hit 22 million users.
- Hacking group claims theft of 1 billion records from Salesforce customer databases – A notorious predominantly English-speaking hacking group has launched a website to extort its victims, threatening to release about a billion records stolen from companies who store their customers’ data in cloud databases hosted by Salesforce.
- The Salesloft-Drift Breach: Analyzing the Biggest SaaS Breach of 2025 – Supply chain attacks that exploit unmonitored SaaS-to-SaaS integrations affect ten times more companies than traditional credential-based breaches.
- DraftKings warns of account breaches in credential stuffing attacks – Sports betting giant DraftKings has notified an undisclosed number of customers that their accounts had been hacked in a recent wave of credential stuffing attacks.
- California enacts law giving consumers ability to universally opt out of data sharing – California Gov. Gavin Newsom on Wednesday signed a bill which requires web browsers to make it easier for Californians to opt-out of allowing third parties to sell their data.
- Fake ‘Inflation Refund’ texts target New Yorkers in new scam – An ongoing smishing campaign is targeting New Yorkers with text messages posing as the Department of Taxation and Finance, claiming to offer “Inflation Refunds” in an attempt to steal victims’ personal and financial data.