Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week.
Featured Analysis
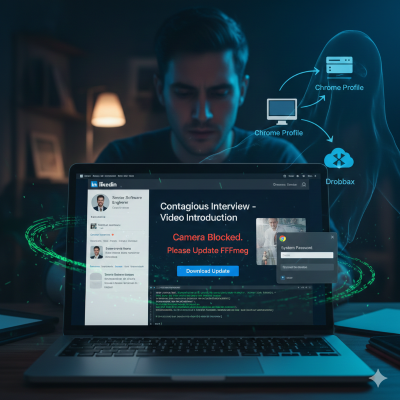
Featured article analysis: Fake LinkedIn jobs trick Mac users into downloading Flexible Ferret malware
This article exposes a targeted and multi-stage social engineering campaign, identified as “Contagious Interview,” which is luring Mac users via fake job postings on LinkedIn. The attackers, posing as recruiters, guide victims to a malicious website under the pretense of a job application requiring a video introduction. This initial stage leverages the professional aspirations of job seekers, particularly in technical fields like software development and cryptocurrency, to establish trust. The sophisticated nature of the attack, which researchers suggest points to the Democratic People’s Republic of Korea (DPRK), demonstrates a high level of planning, relying heavily on human vulnerability rather than just technical exploits.
The core of the attack lies in a clever deception aimed at installing a sophisticated piece of malware. When applicants attempt to record a video, the site falsely claims that camera access is blocked and prompts them to download a supposed “update” for the legitimate FFmpeg media processing software. Following this, the victims are instructed to execute a curl command in their Terminal, a technical step that lends false legitimacy and is highly dangerous. This command downloads a script that installs a Go-based backdoor. Crucially, a subsequent decoy application, disguised as a Chrome prompt, is used to trick the user into entering their system password, which is immediately stolen and sent to the attackers via Dropbox.
The ultimate payload is the Flexible Ferret malware, a multi-stage macOS threat active since early 2025. Once installed, it establishes persistence by creating a LaunchAgent, ensuring it survives system restarts and grants attackers long-term, covert access. This backdoor is highly invasive, giving the cybercriminals capabilities to collect detailed system information, upload and download files, execute shell commands (granting full system control), and specifically target and extract data from Chrome browser profiles. The campaign highlights the increasing trend of sophisticated, persistent malware targeting macOS and serves as a critical warning about the need for extreme caution when dealing with unsolicited communications and instructions to run code, even if delivered through professional platforms.
Projects
- TryHackMe – CAPA: The Basics – In Progress
Articles
- Report Names Teen in Scattered LAPSUS$ Hunters, Group Denies – Scattered LAPSUS$ Hunters admin “Rey,” allegedly a 15-year-old named Saif Khader from Jordan, has been named in a report linking him to the group. He denies the claim.
- Scottish council still rebuilding systems two years after ransomware attack – Audit sympathetic toward Comhairle nan Eilean Siar as staff stretched to capacity trying to recover
- Fake LinkedIn jobs trick Mac users into downloading Flexible Ferret malware – Researchers have discovered a new attack targeting Mac users. It lures them to a fake job website, then tricks them into downloading malware via a bogus software update.
- Ransomware Attack Disrupts Local Emergency Alert System Across US – The OnSolve CodeRED platform has been targeted by the Inc Ransom ransomware group, resulting in disruptions and a data breach.
- FBI: Cybercriminals stole $262M by impersonating bank support teams – The FBI warned today of a massive surge in account takeover (ATO) fraud schemes and said that cybercriminals impersonating financial institutions have stolen over $262 million in ATO attacks since the start of the year.
- CISA: Spyware and RATs used to target WhatsApp and Signal Users – CISA warns that threat actors are actively using commercial spyware and RATs to target users of mobile messaging apps WhatsApp and Signal.
- AI teddy bear for kids responds with sexual content and advice about weapons – In testing, FoloToy’s AI teddy bear jumped from friendly chat to sexual topics and unsafe household advice. It shows how easily artificial intelligence can cross serious boundaries. It’s a fair moment to ask whether AI-powered stuffed animals are appropriate for children.
- Major US Banks Impacted by SitusAMC Hack – Hackers stole corporate data such as accounting records and legal agreements, but did not deploy file-encrypting ransomware.
- FBI: Cybercriminals stole $262M by impersonating bank support teams – The FBI warned today of a massive surge in account takeover (ATO) fraud schemes and said that cybercriminals impersonating financial institutions have stolen over $262 million in ATO attacks since the start of the year.