social engineering
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 2/16/26
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: All U.S. Social Security numbers may need to be changed following a massive
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 1/19/26
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: You Got Phished? Of Course! You’re Human… The BleepingComputer article, “You Got Phished?
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 11/24/25
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: Fake LinkedIn jobs trick Mac users into downloading Flexible Ferret malware This article
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 11/17/25
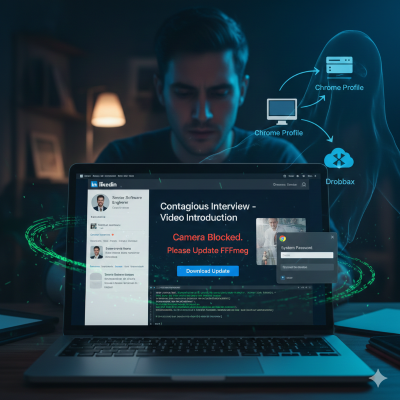
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: Be careful responding to unexpected job interviews This article from Malwarebytes Labs deconstructs
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 11/3/25
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: Hackers use RMM tools to breach freighters and steal cargo shipments This sophisticated
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 10/20/25
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: Verizon: Mobile Blindspot Leads to Needless Data Breaches The analysis of Verizon’s 2025
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 9/22/25
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: Attackers Abuse AI Tools to Generate Fake CAPTCHAs in Phishing Attacks This new research
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 8/25/25
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: Booking.com phishing campaign uses sneaky ‘ん’ character to trick you These are two separate
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 8/18/25
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: HR giant Workday discloses data breach after Salesforce attack Workday, a major human resources
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 7/7/25
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: Elmo’s X account was hacked and shared antisemitic and racist posts The recent