privacy
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 10/6/25
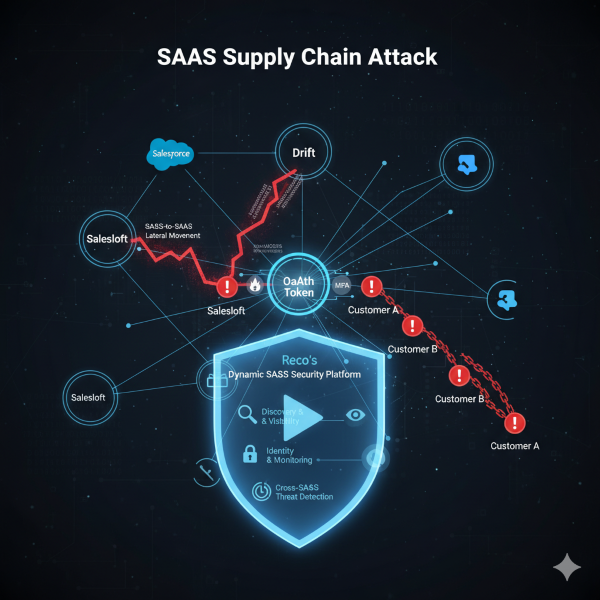
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: The Salesloft-Drift Breach: Analyzing the Biggest SaaS Breach of 2025 Analysis of The
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 7/28/25
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: Tea’s data breach shows why you should be wary of new apps — especially
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 7/14/25
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: McDonald’s Chatbot Recruitment Platform Exposed 64 Million Job Applications This reveals a significant data
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 6/9/25
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: 40,000 Security Cameras Exposed to Remote Hacking Cybersecurity firm Bitsight has unveiled a significant
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 5/12/25
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: Broadcom employee data stolen by ransomware crooks following hit on payroll provider This serves
-
Social Media and Minors
Some great content and interesting conversation around social media and minors (teens, etc.). I wanted to share this as I think it pertains to privacy.