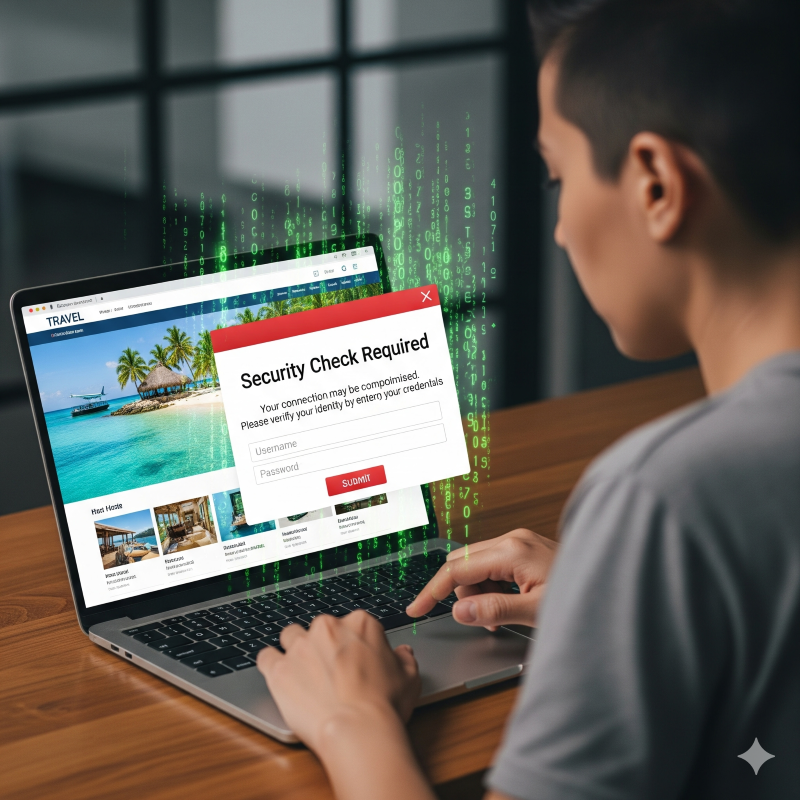
Malware
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 2/9/26
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: The Rise of OpenClaw: AI with Hands OpenClaw, formerly known as Clawdbot and Moltbot,
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 12/8/25
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: Block all AI browsers for the foreseeable future: Gartner Based on the advisory
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 10/13/25
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: Satellites found exposing unencrypted data, including phone calls and some military comms This
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 9/1/25
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: New ClickFix Malware Variant ‘LightPerlGirl’ Targets Users in Stealthy Hack The article highlights
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 8/4/25
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: Hacker extradited to US for stealing $3.3 million from taxpayers The article details the
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 6/9/25
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: 40,000 Security Cameras Exposed to Remote Hacking Cybersecurity firm Bitsight has unveiled a significant