credential stuffing
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 10/6/25
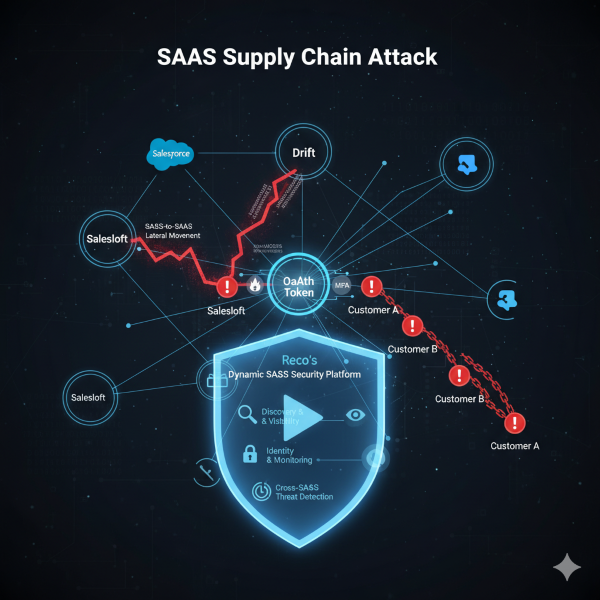
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: The Salesloft-Drift Breach: Analyzing the Biggest SaaS Breach of 2025 Analysis of The
-
What’s New in Cybersecurity This Week: Projects, Videos, Articles & Podcasts I’m Following – 3/24/25
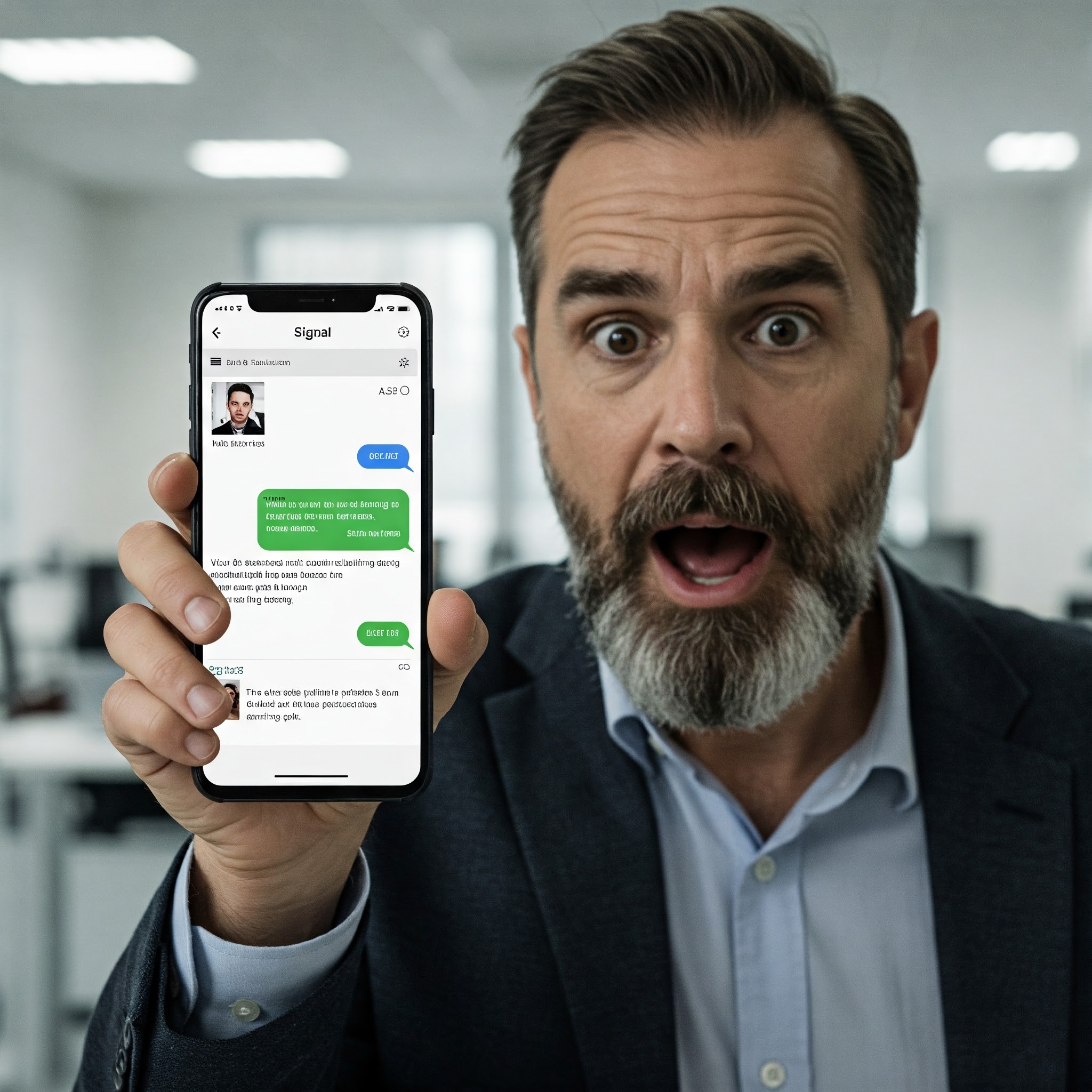
Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week. Featured Analysis Featured article analysis: Mike Waltz takes ‘full responsibility’ for Signal group chat leak The accidental inclusion
-
Smishing Example
What is Smishing? Smishing, a portmanteau of “phishing” and “SMS,” the latter being the protocol used by most phone text messaging services, is a cyberattack that uses misleading text messages to deceive victims. The goal is to trick you into believing that a message has arrived from a trusted person or organization, and then convincing